
Krystal are a UK-based host that offers configurable VPS, Shared and Dedicated packages. There’s not much choice in the UK hosting market so consequently there are some pretty steep prices out there compared to their USA datacentre counterparts. That said, Krystal seem to have all bases covered, let’s take a look at their offerings…
Krystal’s standard hosting features and guarantees
All Krystal plans share a common set of features, like premium control panel and a longer-than-most money-back guarantee. They have been in business since 2002 so they are here to stay and with over 90% of their customers recommending their hosting, it’s a no-brainer decision.
The Krystal difference
Their CEO, Simon Blackler, gives his reasons why they are different to other hosts:
In 2002, frustrated by poor service and bad business practices, I created Krystal to provide an “Honest, Reliable & Personal” alternative to the large faceless hosting corporations. We’re named Krystal because the company embodies values often associated with precious crystals, such as quality, rarity and transparency.
Over the last 15 years our unique approach to business has won us a reputation for excellence and a loyal following.
We’re now the largest independent UK web host and are rated the best web hosting company by popular review sites.We’re in business because we’re passionate about technology and solving problems.
I hope that you’ll join us today and experience the Krystal difference for yourself.
Well, it’s true that many hosts have poor service and some even downright shady business practices, but judging on the reviews coming back from established sites such as Trust Pilot, Krystal are a force to be reckoned with.
At the time of writing, Krystal offer entry-level hosting for £3.99 monthly with these features:
- FREE 256-bit SSL certificate
- FREE website builder
- 100% SSD cloud hosting
- Unlimited bandwidth
- Optimised for WordPress & more
There’s a configurable VPS from £9.99 monthly with these features:
- 100% SSD cloud VPS
- Full root access
- Free DDoS protection
- Free dedicated IP
- No setup fee
For businesses requiring PCI compliance, £29.99 monthly gets you:
- Fully PCI-DSS Compliant
- FREE DDoS protection
- FREE 256-bit SSL certificate
- FREE backups every 6 hours
- FREE domain name for life
The big plus is that you get a 60 day money back guarantee with everything, so a full refund can be had and you lose nothing (except your time testing their servers). In our experience you’ll probably stay with them as the ping times are as good as anything we have seen on the UK market and server configuration options are up there with the best.
Verdict
What we really like is the company’s transparency. They are trying to do things differently and succeeding – a refreshing thing in the murky world of hosting. They use green technology, which means 100% renewable energy at all of their sites, which we love because reducing the impact of these datacentres is a must.
With a more-than-standard offering, Krystal have certainly raised the bar. For the price-conscious, the VPS and dedicated prices are spot-on, being considerably cheaper than the opposition such as FastHosts, Rackspace, Ionos, 123-Reg and more (comparison reviews coming soon). There’s 24/7 ticket and email support, extremely friendly telephone support (10:00 to 17:00 UK time), cPanel, free migration assistance, automated backups, PHP (5.6 to current) and all the usual stuff like MySQL, PHPMyAdmin, SSH and even the ubiquitous Softaculous. What isn’t there to like? Click the link below to get hosting from what we believe is the best available for UK hosts:
As a Krystal Associate I earn from qualifying purchases read more


 To reset the Administrator password on your Windows server 2012 installation, you’ll need to do the following:
To reset the Administrator password on your Windows server 2012 installation, you’ll need to do the following: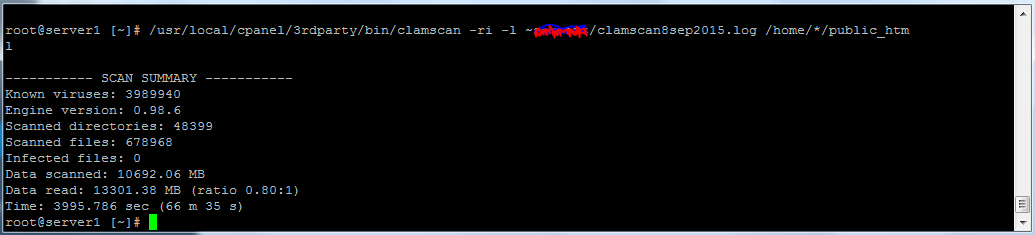
 In this series of articles I am trying to help server admins and owners of VPS or Dedicated servers to find viruses or malware on their servers. Part of the diagnosis of your system is to see what emails are being sent out and from which accounts. Since spammers like to use compromised servers, I believe that it makes sense to check regularly that the emails being sent out roughly match what you would expect to see.
In this series of articles I am trying to help server admins and owners of VPS or Dedicated servers to find viruses or malware on their servers. Part of the diagnosis of your system is to see what emails are being sent out and from which accounts. Since spammers like to use compromised servers, I believe that it makes sense to check regularly that the emails being sent out roughly match what you would expect to see.
 Online backup just got a whole lot cheaper with the latest coupon code from Mozy. Click the link below and type in the coupon code ENCRYPTION for 20% discount:
Online backup just got a whole lot cheaper with the latest coupon code from Mozy. Click the link below and type in the coupon code ENCRYPTION for 20% discount: